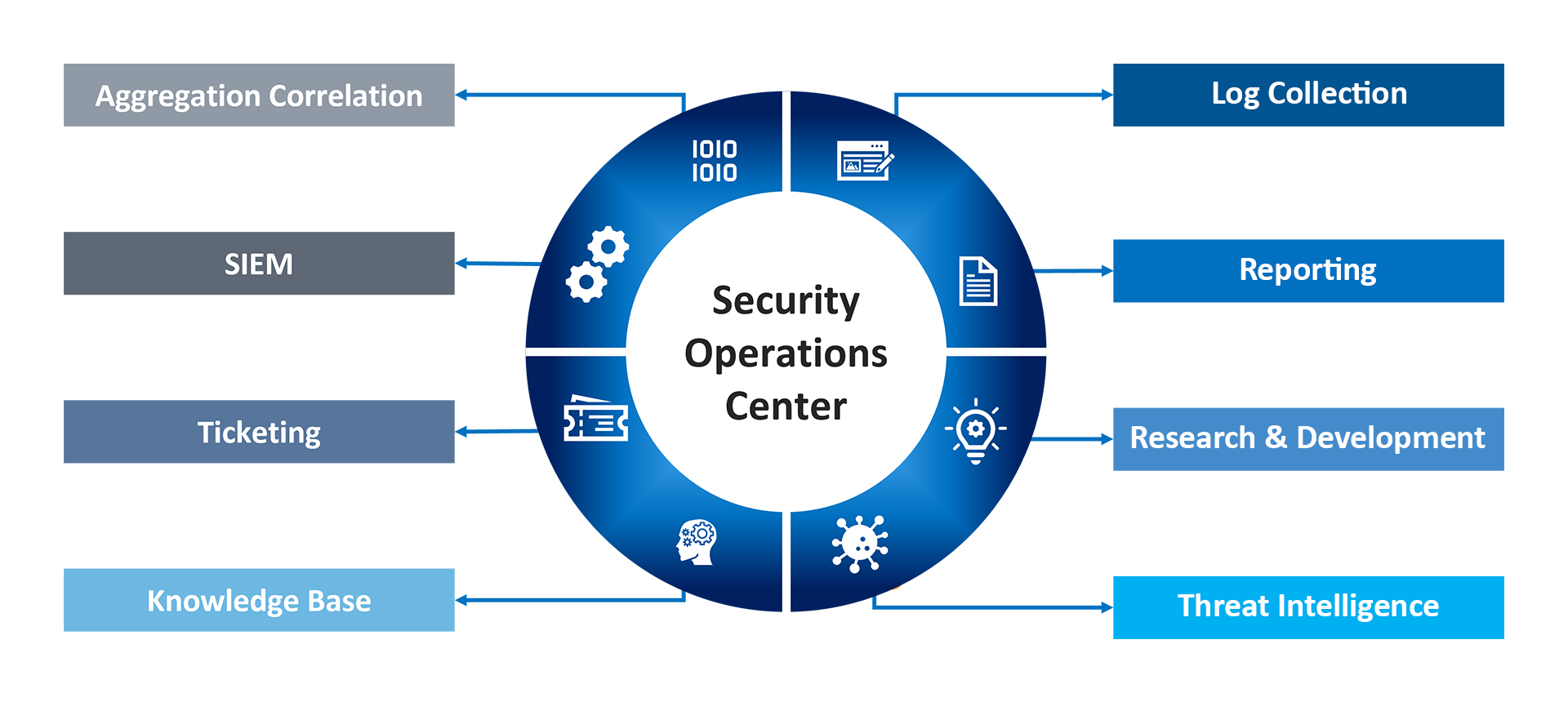
The MOURI Tech SOC Solution Approach
Technology
Built From the Ground Up
- Telemetry
- SIEM, SOAR, UEBA, NBA, EDR
- Threat Intelligence
- Sandbox, Deception, Response Orchestration
- 3rd Party Integrations
Process
Operationalizing a SOC
- Identification: Detection, Analysis
- Remediation: Containment, Eradication and Recover process
- Continuous 24/7 Threat Monitoring
- Centralize Log or Information Aggregation and Analysis
- Key Risk Indicators Measuring

People
A Blue Team Composition
- SOC Analysts, Incident Responder
- SOC architects, Threat Hunters
- Compliance Analyst
- Red Team and Purple Team
- Cyber Threat Intelligence Team